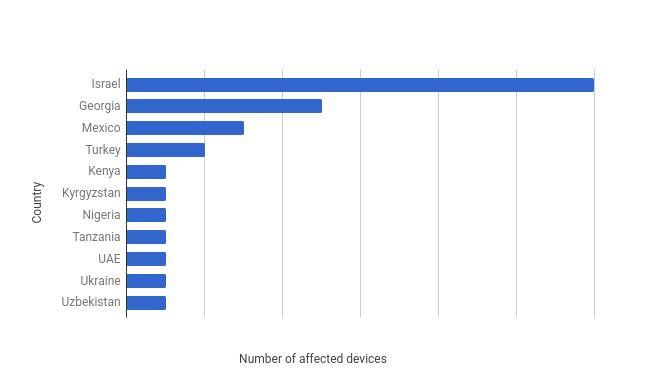
Since the revelations of Snowden on the espionage campaigns carried out by American governments, companies are increasingly turning to encryption tools to strengthen the security of their equipment and thus avoid leaks of data of data.Since the increasingly generalized adoption of these tools, two groups have clashed openly with defenders who highlight the safety and privacy of users and detractors who point out that they can be used by malicious actorsTo escape the surveillance of the police.Aware that there is a niche to be exploited with entities who wish to access user information despite encryption mechanisms and other safety tools used, another market is developing on the fringes of these tools in order to meet the demand forthe latter (governments and other actors with important financial resources) who wish to monitor people in all discretion by bypassing security systems such as data encryption.Last year, Ahmed Mansoor, a human rights defender living in the United Arab Emirates (water), received an SMS on his iPhone who suggested clicking on a link to have information on prisoners tortured inPrisons of the United Arab Emirates.After transferring the message to Citizen Lab, the organization's safety researchers as well as those of Lookout, the publisher of security solutions for businesses and individuals, discovered that behind this message was hiding Pegasus, one of the SpywareThe most sophisticated ever encountered which has been used to spy on iPhone users for several years.To do this, Pegasus used three flaws (trident) of Zero Day type in order to jailbreaker the targeted device and to recover data of all kinds on the infected iPhone.Since then, Apple has released a fix to correct the exploits used by Pegasus to infect its mobile system.But this discovery fairly beneficial for iPhone users whose episode with Pegasus seemed to be completed after the release of the correction gave rise to the discovery of signs of abnormal applications from the data analyzed by the researchers of Lookout.Intrigued, these researchers have alerted Google and since then, a hunt has been undertaken on both sides of companies that have not hesitated to share the information acquired.This resulted in the discovery of the presence of spy software (Spyware) considered by Lookout as a variant of Pegasus for Android and baptized Chrysaor by Google.For a few hours, Lookout and Google have concomitantly published press releases to alert users to this new discovery threat which endangers the confidentiality of information from Android users.According to the two companies, this Spyware was developed by NSO Group Technologies, a company based in Israel and created in 2010 with the aim of developing and selling cyberarms to governments in order to help them fight terrorism and crime.In 2013, the company's turnover was 40 million.Two years later, that is to say in 2015, this turnover has more than tripled by going to $ 150 million.Based on these figures, it is an understatement to say that this market is booming with customers who are increasingly using third -party companies to spy on users.Regarding Pegasus Android version, one of the things that reassure is that this spyware has been discovered in activity on less than three dozen devices in some countries such as Israel, Georgia, Mexico, Turkey, Water, Kenya, Nigeria, Ukraine and several other countries.Immediately, Google contacted users of devices infected with this variant of PEGASUS after identifying the total number of these devices.To settle on Android devices, Google believes that the attackers would certainly have convinced users in one way or another to get them to download the malicious software on their devices.And once installed, the Spyware uses the Framaroot technique for "; Rooter;"the targeted device and have total control of it.This version of Pegasus therefore does not use Zero Day faults to root Android devices as was the case with the iOS version.In addition, on iOS, when the spyware does not manage to jailbreaker the targeted device, the infection cannot take place.But for the case of Android, if the Spyware fails to root the device with the features, it uses a binary of superuser on the Android system to raise its privileges in order to have access to the data andExport them to the distant servers of the attackers.Whether by rooting the phone or using high privileges, when the Spyware manages to infect the target, the attackers can use it to carry out the following operations: finally, you should know that this variant of Pegasus is not amalware like all the others.Where many malicious software would try to stay at all costs on the infected device, Pegasus is automatically destroyed if he analyzes and concludes that his position on the device is at risk.In addition, several other scenarios have been detected where this variant of Pegasus is deleted by itself.We have for example the case where the country's code on the mobile associated with the SIM card is invalid.When he also detects an antidote at the location /sdcard /memosnotes, he destroys himself.When Pegasus for Android has not managed to connect to the servers after 60 days or when he receives a specific order from the order and control server, it automatically deletes.To protect themselves, Google explains that the installation of any additional application is necessary.To stay protected, just follow the basic instructions such as install applications only from known sources like Google Play, activate the device locking with a PIN code, a password or a diagram, putday its device, make sure that the Google Verify apps tool is activated on the device and enter your device in the Android devices manager to secure its data in the event of loss or flight of its device.Source : Lookout, GoogleEt vous ?Que pensez-vous de la découverte de cette faille ?Les utilisateurs Android devraient-ils se sentir rassurés ou plutôt être inquiets ?Voir aussi Apple corrige en urgence trois vulnérabilités zero day sur iOS qui ont permis à un logiciel espion de passer sous les radars pendant des années Des documents du NSO Group indiquent comment l'entreprise choisit les clients à qui elle vend son spyware, mais aussi le montant de la facture La Rubrique Android, Forum Android, Cours et tutoriels Android, FAQ Android









SOS Public Hospital: our revelation...
The best smartphones for gaming in...
Google Maps: activate the new widge...
Free tips in video: Free Mobile off...